Hey Readers! Welcome to trendphobia. In today’s digitally driven world ransomware attacks have become a pervasive and costly threat to individuals, businesses and organizations of all sizes. When faced with a ransomware attack victims are often left with a difficult decision pay the ransom demanded by the hackers or find another way to recover their data. While experts strongly advise against paying ransoms, there are situations where negotiation might be the only viable option. In this blog post, we’ll explore the steps to negotiate with ransomware hackers effectively.
Step 1: Assess the Situation

Before considering negotiation it’s crucial to thoroughly assess the situation:
- Confirm It’s Ransomware: Ensure that your systems are indeed compromised by ransomware. Sometimes, what seems like ransomware might be a different issue.
- Backup Data: Check if you have recent backups of your data. If you do you might not need to negotiate at all.
- Identify the Ransomware: Determine the specific ransomware variant used. Some ransomware strains have known decryption tools available.
Step 2: Consult with Experts
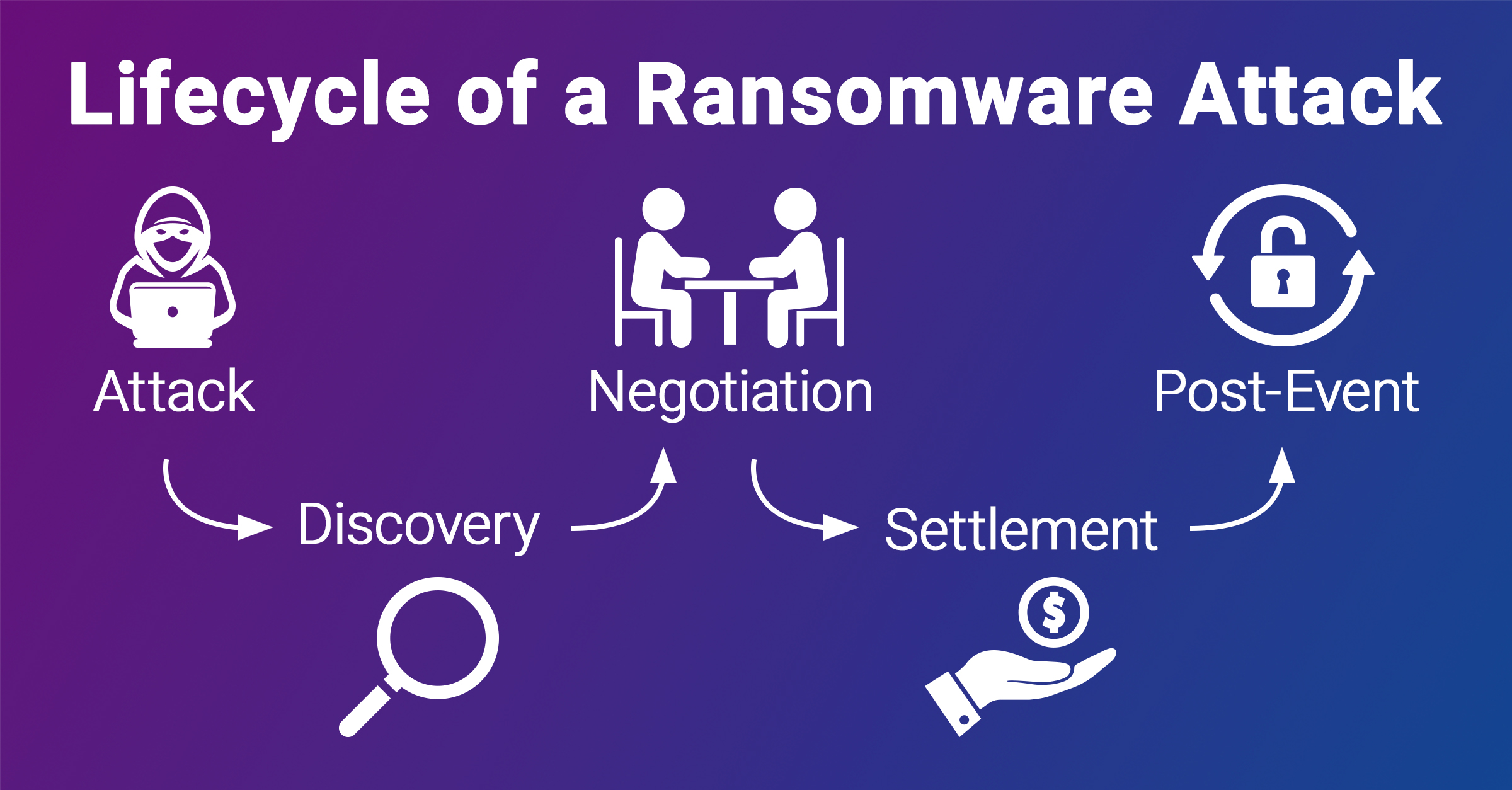
Ransomware attacks are complex and the wrong move can worsen the situation. Therefore, it is crucial to consult with cybersecurity experts, law enforcement agencies or a reputable incident response team to assess the severity and explore possible alternatives.
Step 3: Establish Contact

If after consulting experts it’s determined that negotiation is necessary take these steps to establish contact with the hackers:
- Use a Secure Channel: Create a dedicated, secure and anonymous communication channel to interact with the attackers. Avoid using your regular email or phone.
- Maintain Professionalism: Approach the negotiation with professionalism and a calm demeanor. Avoid anger or threats as this can escalate the situation.
Also read E-Banking: Transforming Financial Landscapes
Step 4: Verify Data Access

Before negotiations proceed, request proof that the hackers can decrypt your data. This might involve them decrypting a small less critical file to demonstrate their capabilities.
Step 5: Determine the Terms

- Ransom Amount: Negotiate the ransom amount, keeping in mind that paying it doesn’t guarantee the safe return of your data.
- Payment Method: Discuss the method of payment. Cryptocurrencies like Bitcoin are often favored by hackers due to their anonymity.
- Timeline: Set clear deadlines for payment and data decryption.
Step 6: Payment and Data Recovery

If you decide to pay the ransom follow these guidelines:
- Document Everything: Keep records of all communications, payments and decryption keys provided by the hackers.
- Payment Anonymity: Use a trusted third party to facilitate the payment if possible to protect your identity.
- Decrypt and Verify: After receiving the decryption key, carefully decrypt and verify your data before taking any other actions.
Also read What Is Python Programming?
Step 7: Strengthen Security
- Patch Vulnerabilities: Update and patch all software and systems regularly.
- Enhance Security Measures: Invest in robust cybersecurity solutions, employee training and security best practices.
- Backup Strategy: Implement a secure and regularly updated backup strategy.

Conclusion
Prevention and preparation are the best defenses against ransomware attacks. Regularly back up your data, keep your systems updated and invest in robust cybersecurity measures to minimize the risk of falling victim to ransomware in the first place. Remember, paying ransoms not only funds criminal activities but also doesn’t guarantee the safe return of your data. Reporting the attack to law enforcement agencies is essential to combat these cybercriminals and protect others from becoming victims.
For more Interesting Tech blog follow Trendphobia.
Thanks for reading
Also read:
- ChatGPT vs. Writers: Will AI take over content writer?
- Metamorphic Robots: The Shape-Shifting Future of Robotics
- Defeating Phishing Attacks: A Guide to Secure Online Navigation
- The Telettrofono: World’s First Mobile Phone
- Airborne Internet: Bridging the Digital Divide
